A new worm has hit the Internet and its taking its toll on computers worldwide. It has been reported that over 9 million computers have already been infected.
The worm called “Downandup”, “Conficker” or “Kido” by different anti-virus vendors uses the Microsoft vulnerability which I blogged about here (Worm Takes Advantage Of Microsoft Flaw) and here (Microsoft Releases Emergency Patch).
The worm mostly spreads across networks, turning off the system restore and deleting the restore points, blocks access to security website, download additional malware from the author, attempts to infect other computers by scanning network shares and scheduled a task to re-infect the computer if removed.
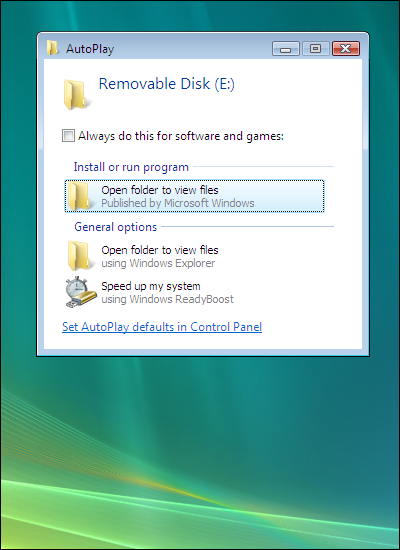
What is interesting is that it can also spread by USB memory keys or devices making use of social engineering which makes it more dangerous to the untrained eye. When a USB drive is inserted it shows a modified AutoPlay screen seen below which will install the worm when the users inadvertently clicks on it.
According to SANS Internet Storm Center, one of the reasons the worm is infecting so many machines is that “Conficker” uses multiple infection vectors:
- It exploits the MS08-067 vulnerability,
- It brute forces Administrator passwords on local networks and spreads through ADMIN$ shares and finally
- It infects removable devices and network shares by creating a special autorun.inf file and dropping its own DLL on the device.
Characteristics –
When executed, the worm copies itself using a random name to the %Sysdir% folder.
(Where %Sysdir% is the Windows system folder; e.g. C:\Windows\System32)
It modifies the following registry key to create a randomly-named service on the affected syetem:
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\{random}\Parameters\”ServiceDll” = “Path to worm”
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\{random}\”ImagePath” = %SystemRoot%\system32\svchost.exe -k netsvcs
Attempts connections to one or more of the following websites to obtain the public ip address of the affected computer.
- hxxp://www.getmyip.org
- hxxp://getmyip.co.uk
- hxxp://checkip.dyndns.org
- hxxp://whatsmyipaddress.com
Attempts to download a malware file from the remote website: (Rogue Russian site is up but not serving file anymore)
- hxxp://trafficconverter.biz/[Removed]antispyware/[Removed].exe
Starts a HTTP server on a random port on the infected machine to host a copy of the worm.
Continuously scans the subnet of the infected host for vulnerable machines and executes the exploit. If the exploit is successful, the remote computer will then connect back to the http server and download a copy of the worm.
Later variants of w32/Conficker.worm are using scheduled tasks and Autorun.inf file to replicate on to non vulnerable systems or to reinfect previously infected systems after they have been cleaned.
Suggestions –
- Disable AutoPlay in your environment.
- Run a good security suite.
- Keep your computer updated with the latest patches.
- Be PROACTIVE and look for the worm in your environment.
Sources:
http://www.nai.com
http://www.symantec.com
http://www.f-secure.com
http://isc.sans.org
[ad]