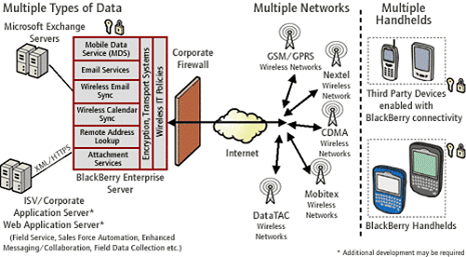
The policy below provides an example of security measures that should be taken towards protecting a corporate network from the threats presented by mobile devices.
These configurations and options should be “taken with a grain of salt”; as a guideline to what features should be set to mitigate the risk of smart-phone being used as un-metered gateways into the corporate network.
The 5-step process should be put into action to address security issues related to smart-phones.
- Identify threats and vulnerabilities.
- Measure the risk.
- Determine what control should be put in place.
- Implement industry best practices and standards.
- Develop and communicate policy and awareness.
THE SAMPLE POLICY:
Device-Only Items:
Password Required: True
Allow Peer-to-Peer Messages: False (This can be set to be audited if enabled)
Minimum Password Length: 4
User Can Disable Password: False
Maximum Security Timeout: 5
Maximum Password Age: 180
User Can Change Timeout: False
Password Pattern Checks: (used to enforce complexity in passwords)
Enable Long-Term Timeout: True
Allow SMS: False (These can be set be audited if enabled)
Enable WAP Config: False
Desktop-Only Items:
Show Application Loader: False
Force Load Count: 0
Auto Backup Enabled: True
Auto Backup Include All: True
Do Not Save Sent Messages: False
Common Policy Group:
Lock Owner Info: Lock Information Text
IT Policy Notification:
Set Owner Info: (If found please return to message……)
Disable MMS: True
Password Policy Group:
Set Password Timeout: 20
Set Maximum Password Attempts: 5
Suppress Password Echo: True
Maximum Password History: 3
Security Policy Group:
Disable Untrusted Certificate Use: True
Disabled Revoked Certificate Use: True
Disable Peer-to-Peer Normal Send: True
Disable Key Store Low Security: True
Certificate Status Cache Timeout: 1
Disallow Third Party Application Download: True
Force Lock When Holstered: True
Allow Third Party Apps to Use Serial Port: False
Disable Invalid Certificate Use: True
Disable Weak Certificate Use: True
Disable Key Store Backup: True
Certificate Status Maximum Expiry Time: 4
Disable Stale Status Use: True
Disable Cut/Copy/Paste: True
Disable Radio When Cradled: True
Disable Forwarding Between Services: True
Disabled Unverified CRLs: True
Disable 3DES Transport Crypto: False
Disable Persisted Plain Text: True
Disable Unverified Certificate use: True
Disable IP Modem: True
Allow Smart Card Password Caching: False
SMIME Application Policy Group:
SMIME Minimum Strong RSA Key Length: 1024
SMIME Minimum Strong DH Key Length: 1024
SMIME Minimum Strong ECC Key Length: 163
SMIME Allowed Content Ciphers: AES (256-bit), Triple DES
SMIME Minimum Strong DSA Key Length: 1024
Memory Cleaner Policy Group:
Memory Cleaner Maximum Idle Time: 10
Force Memory Cleaner When Holstered: True
TLS Application Policy Group:
TLS Disable Weak Ciphers: Disable weak ciphers
TLS Disable Untrusted Connection: Disable untrusted connections
TLS Minimum Strong RSA Key Length: 1024
TLS Minimum Strong DH Key Length: 1024
TLS Minimum Strong ECC Key Length: 163
TLS Disable Invalid Connection: Disable invalid connections
TLS Minimum Strong DSA Key Length: 1024
TLS Device Side Only: False
WTLS Application Policy Group:
WTLS Disable Weak Ciphers: Disable weak ciphers
WTLS Disable Untrusted Connection: Disable untrusted connections
WTLS Minimum Strong RSA Key Length: 1024
WTLS Minimum Strong DH Ley Lenth: 1024
WTLS Minimum Strong ECC: 163
WTLS Disable Invalid Connection: Disable invalid connections
Browser Policy Group:
Allow BIS Browser: False
PIM Sync Policy Group:
Disable PIN Messages Wireless Sync: False
Disable SMS Messages Wireless Sync: False
Desktop Policy Group:
Desktop Password Cache Timeout: 10
Desktop Allow Desktop Add-ins: False
Desktop Allow Device Switch: False
Locking Down The Blackberry Network
Auditing SMS and PIN Messages on a BES
[ad]