I recently wrote about Secure Internet Browsing and the need for it. Not too long thereafter I found an instance were you might want to make sure that your traffic is anonymous so I will take a closer look at “Onion Routing” and “Tor”.
I recently wrote about Secure Internet Browsing and the need for it. Not too long thereafter I found an instance were you might want to make sure that your traffic is anonymous so I will take a closer look at “Onion Routing” and “Tor”.
Tor is a software project that helps you defend against traffic analysis, a form of network surveillance that threatens personal freedom and privacy, confidential business activities and relationships, and state security. Tor protects you by bouncing your communications around a distributed network of relays run by volunteers all around the world: it prevents somebody watching your Internet connection from learning what sites you visit, and it prevents the sites you visit from learning your physical location. Tor works with many of your existing applications, including web browsers, instant messaging clients, remote login, and other applications based on the TCP protocol.
There are several ports of the “Tor” project out there and after evaluating several of them the better one seems to be the Vidalia-Tor-Privoxy Bundle here.
There are several components in this package that warrant explanation.
The Vidalia application is a GUI program to access Tor.
Then we have Tor which uses cryptography in a layered manner working at the TCP stream level as opposed to using application layer solutions like anonymous proxies. Is important to note that Tor (onion routing) is designed to anonymize traffic and does NOT secure it. Additionally there could be some weaknesses that I will address later on DNS leaks, IP address leakage and cookie leakage.
The next component of the bundle is Privoxy which is a non-caching web proxy with advanced filtering capabilities for enhancing privacy listening on port TCP 8118. Privoxy receives requests from the web browser and then forwards web traffic to through the Tor network for anonymity. Tor sits on your PC listening on port TCP 9050 ready to scrub the traffic clean from traffic analysis.
Finally there is TorButton (add-on) which enables Firefox users to enable/disable the use of Tor by the browser with just one click.
I chose not to select this during the install since it has mixed reviews due to bugs and decided to go with a much better add-on called QuickProxy.
There is little you need to do to the default install. You should see Privoxy running on your “Systray” as a blue “P” icon and next to it you should see a “green onion” icon. Clicking on the “green onion” will bring up the Vidalia Control Panel so you can connect to the Tor network.
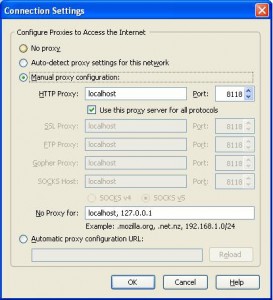
The last thing that needs to be done is to configure your browser to point to the local proxy (Privoxy) running on your PC as shown below.
Click on the Image to enlarge.
At the button of your Firefox browser you should see a Green/Red “P” (QuickProxy) which determines if the proxy is selected or not.
Finally to test if your browser is anonymized. Make sure your Firefox status bar shows the Red “P” and go to http://www.ipchicken.com to determine your IP address. Click on the “P” icon and watch it turn to green and then proceed to refresh your browser and your IP address should change to something random.

Now lets look at the weaknesses starting with DNS leaks.
The Problem: When your applications connect to servers on the Internet, they need to resolve hostnames that you can read (like www.torproject.org) into IP addresses that the Internet can use (like 209.237.230.66). To do this, your application sends a request to a DNS server, telling it the hostname it wants to resolve. The DNS server replies by telling your application the IP address.
Clearly, this is a bad idea if you plan to connect to the remote host anonymously: when your application sends the request to the DNS server, the DNS server (and anybody else who might be watching) can see what hostname you are asking for. Even if your application then uses Tor to connect to the IP anonymously, it will be pretty obvious that the user making the anonymous connection is probably the same person who made the DNS request.
Using Tor in concert with Privoxy pretty much takes care of this, since its a socks4a-capable HTTP proxy but if you intend to anonymize other non-SOCKS aware applications (for instant messaging, Jabber, IRC, etc), that are connected directly to Tor using SOCKS 4 of SOCKS 5 you will be prone to DNS leaks and not be as anonymous as you might think.
The Tor project is working to resolve this in their next release by including a DNS resolver that will send queries over the mixed network.
Alternatively you can modify how Firefox performs DNS lookups which is generally done by handing down the request to the operating system.
To force DNS requests into the Tor channel, visit the special URL
about:configand find the keynetwork.proxy.socks_remote_dns. Set it totrue
Now what about cookie leakages.
Websites are allowed unless specifically told otherwise to store bits of information on your PC, to determine its you the next you visit. This allows for a more fluent and pleasant experience on any site you log into.
Now when you want to disassociate yourself from your identity it presents a problem. When you visit a website that has already placed a cookie on your computer and then you visit it again with your Tor identity, the website can determine that even though the originating IP addresses are different, it is in fact the same person. Making sure you have a second Firefox account or have erased your cookies becomes paramount to maintain your identities separate.
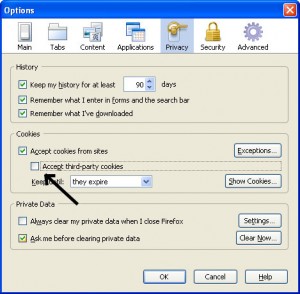
Additionally you have to worry about cross-site cookies which can be solved by allowing cookies for the originating website only, and have them kept only until Firefox is closed as seen below.
Click on the Image to enlarge.
Finally a word on security.
As Tor relies on a network of people around the world serving as relays to the traffic, you can easily see how a particular request to a website sending over a clear channel a username/password combination might be problematic. Someone actually listening (Tor Relay) to the traffic relayed through them will be able to pick up this information.
Even worse scenario would be someone phishing for information at an exit node and pretending to be a website you are visiting.
The most simple solution for this is to only use SSL and forcing Firefox to tell you if you are about to send information to an un-encrypted website.
Turn on warnings for secure and insecure sites. At the Firefox configuration URL about:config, find the keys beginning with security.warn_. Set all of them to true, except for the once ending in .show_once, which should be set to false. Then set security.warn_entering_secure to false — you really don’t need to be alerted to that.
If you visit a site and the browser tells you that the SSL certificate may be invalid, don’t trust it!
[ad]
Sources:
Wikipedia
The Tor Project