 Early last year India threatened to discontinue Blackberry service if Research In Motion (RIM), the company behind the Blackberry did not allow the Indian Government to monitor the Blackberry network traffic raising serious security concerns. Here are a few articles from PCWorld, InfoWorld, and CNet.
Early last year India threatened to discontinue Blackberry service if Research In Motion (RIM), the company behind the Blackberry did not allow the Indian Government to monitor the Blackberry network traffic raising serious security concerns. Here are a few articles from PCWorld, InfoWorld, and CNet.
Now president-elect Barack Obama vows to keep his Blackberry despite hacking fears and concerns by the Secret Service.
This will not only be a headache for the Secret Service but its pretty likely that hacking attempts towards the RIM network will increase exponentially.
Generally people just don’t think about the risk that a smart-phone poses, specially if its connected to a Blackberry Enterprise Server. How could my phone be a risk to anyone? Well a smartphone is not just a phone, but rather a miniature computer that is not just capable of making calls but it also an un-metered gateway into the corporate network.
In order to understand what actions to take to protect a smart-phone, in particular the Blackberry you have to understand how it works and how it interacts with the Blackberry Enterprise Server.
Vulnerabilities:
- Lack of authentication
- Lack of encryption
- Lack of mobile code execution controls
- Difficult to enforce controls
- Peripheral devices introduce additional vulnerabilities
- Infrastructure vulnerabilities service specific operating systems, platforms, applications, etc.
- Small size is prone to theft and loss
- All devices may not be corporate owned
- Multiple configurations of the Blackberry Enterprise Server (BES) architecture
- Limited centralized update mechanisms
- Limited IT/CIO Control
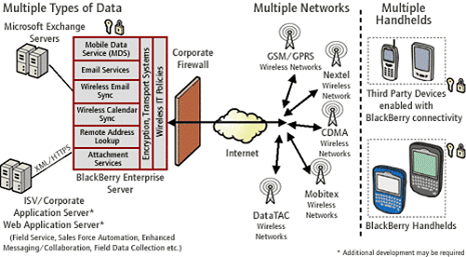
Sources of Recommended Controls and Security Guidelines:
- The Vendor (Microsoft, Treo, RIM, etc.)
- SANS (www.sans.org)
- NIST has a great publication
- Other existing guidelines
- 3rd Party Solutions often fill the gaps
Once the vulnerabilities have been identified we proceed to implement controls and audits.
Controls:
Controls will include policies, standards, practices, procedures, guidelines, awareness, authentication, encryption, and asset management.
Audits:
Once the scope has been defined, allow to review the implementation of policies between the BES, servers, Blackberry devices, and Blackberry desktop agents. Audits also allow the review of configuration and options to ensure that security is not just available but implemented. Additionally configurations pushed down to end devices need to be audited as well.
The infrastructure design and configuration of network components (firewalls, routers, switches, VLANs, etc.) will need to be audited as they play an intricate part of the overall security of the system.
Risk Assessment:
Although this requires additional resources and expertise, its a must in certain environments like corporate or government. A risk assessment will identity security vulnerabilities and provide a 2nd chance to identify all “assets”.
Once this has been completed, validating the risk by performing an “ethical hack” will remove any uncertainty by proving the vulnerabilities identified actually exist.
Conclusion:
Providing documentation on the findings is vital. The documentation required will contain an executive summary, action items and details for system administrators, and a clear and concise report with both the good and the bad findings.
A couple of things that should not fall through the cracks are ensuring that the corrective actions are implementable within the organization and the next audit scheduled.
Sample Policy:
Sample Blackberry Enterprise Server Policy
[ad]

![Reblog this post [with Zemanta]](https://img.zemanta.com/reblog_e.png?x-id=08628cdd-9bdb-4841-ab75-d6bf879ff5f0)



